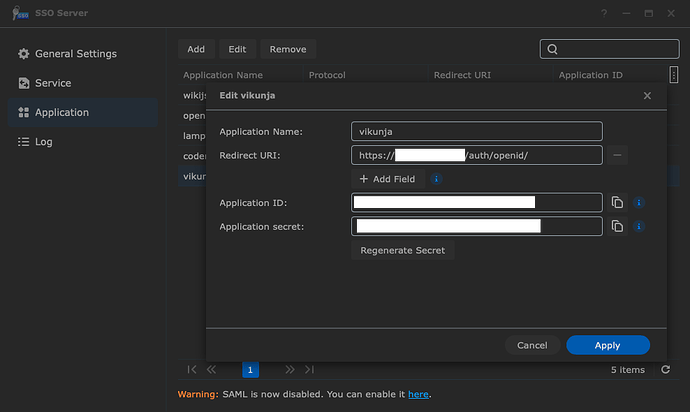
Hi all,
I am trying to set up authentication using the SSO server from my Diskstation. It seems not many users know that there’s OpenID service built in to their Synology, since there is almost no mentions or tutorials on the web. Via trial and error I managed to get a bunch of web apps working with it already and it works great - so far! I am not sure if I’m doing it wrong in this case or if it’s just not compatible with certain apps.
Basic setup was done through docker compose, and both containers are running healthy. I can access the web interface via reverse proxy, do all the basic tasks, send out emails etc. except the OpenID login would never show up.
Maybe someone can point me in the right direction? I pasted the relevant sections below.
service:
enableregistration: false
openid:
enabled: true
redirecturl: https://vikunja.domain.tld/auth/openid/
providers:
- name: OpenID
authurl: https://id.domain.tld/webman/sso
clientid: xxx
clientsecret: xxx
And here what is being returned when calling /.well-known/openid-configuration manually:
{
"authorization_endpoint" : "https://id.domain.tld/webman/sso/SSOOauth.cgi",
"claims_supported" : [ "aud", "email", "exp", "groups", "iat", "iss", "sub", "username" ],
"code_challenge_methods_supported" : [ "S256", "plain" ],
"grant_types_supported" : [ "authorization_code", "implicit" ],
"id_token_signing_alg_values_supported" : [ "RS256" ],
"issuer" : "https://id.domain.tld/webman/sso",
"jwks_uri" : "https://id.domain.tld/webman/sso/openid-jwks.json",
"response_types_supported" : [ "code", "code id_token", "id_token", "id_token token" ],
"scopes_supported" : [ "email", "groups", "openid" ],
"subject_types_supported" : [ "public" ],
"token_endpoint" : "https://id. domain.tld/webman/sso/SSOAccessToken.cgi",
"token_endpoint_auth_methods_supported" : [ "client_secret_basic", "client_secret_post" ],
"userinfo_endpoint" : "https://id. domain.tld/webman/sso/SSOUserInfo.cgi"
}