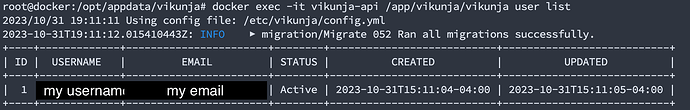
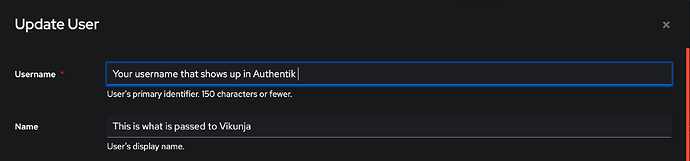
I have an identical config.yml, that returns:
"openid_connect":{"enabled":false,"providers":null}
Just started implementing this today, using the unstable build, any tips?
Edit: decided to Rtfm and will try adding scopes to my authentik and report back
2nd edit: adding vikunja_scopes etc did not work. here is my config
Config.yml
service:
# The public facing URL where your users can reach Vikunja. Used in emails and for the communication between api and frontend.
publicurl: "https://tld"
rootpath: "/etc/vikunja/"
log:
# A folder where all the logfiles should go.
path: <rootpath>logs
# Whether to show any logging at all or none
enabled: true
# Where the normal log should go. Possible values are stdout, stderr, file or off to disable standard logging.
standard: "stdout"
# Change the log level. Possible values (case-insensitive) are CRITICAL, ERROR, WARNING, NOTICE, INFO, DEBUG.
level: "DEBUG"
# Whether or not to log database queries. Useful for debugging. Possible values are stdout, stderr, file or off to disable database logging.
database: "stdout"
# The log level for database log messages. Possible values (case-insensitive) are CRITICAL, ERROR, WARNING, NOTICE, INFO, DEBUG.
databaselevel: "DEBUG"
# Whether to log http requests or not. Possible values are stdout, stderr, file or off to disable http logging.
http: "stdout"
# Echo has its own logging which usually is unnecessary, which is why it is disabled by default. Possible values are stdout, stderr, file or off to disable sta>
echo: "stdout"
# Whether or not to log events. Useful for debugging. Possible values are stdout, stderr, file or off to disable events logging.
events: "stdout"
# The log level for event log messages. Possible values (case-insensitive) are ERROR, INFO, DEBUG.
eventslevel: "DEBUG"
# Whether or not to log mail log messages. This will not log mail contents. Possible values are stdout, stderr, file or off to disable mail-related logging.
mail: "off"
# The log level for mail log messages. Possible values (case-insensitive) are ERROR, WARNING, INFO, DEBUG.
maillevel: "info"
cors:
enable: true
origins:
- "*"
migration:
todoist:
# Wheter to enable the todoist migrator or not
enable: true
# The client id, required for making requests to the todoist api
# You need to register your vikunja instance at https://developer.todoist.com/appconsole.html to get this
clientid: <scrubbed>
# The client secret, also required for making requests to the todoist api
clientsecret: <scrubbed>
# The url where clients are redirected after they authorized Vikunja to access their todoist items.
# This needs to match the url you entered when registering your Vikunja instance at todoist.
# This is usually the frontend url where the frontend then makes a request to /migration/todoist/migrate
# with the code obtained from the todoist api.
# Note that the vikunja frontend expects this to be /migrate/todoist
redirecturl: <frontend url>/migrate/todoist
auth:
# Local authentication will let users log in and register (if enabled) through the db.
# This is the default auth mechanism and does not require any additional configuration.
local:
# Enable or disable local authentication
enabled: false
# OpenID configuration will allow users to authenticate through a third-party OpenID Connect compatible provider.<br/>
```# The provider needs to support the `openid`, `profile` and `email` scopes.<br/>
# **Note:** Some openid providers (like gitlab) only make the email of the user available through openid claims if they have set it to be publicly visible.
# If the email is not public in those cases, authenticating will fail.
# **Note 2:** The frontend expects to be redirected after authentication by the third party
# to <frontend-url>/auth/openid/<auth key>. Please make sure to configure the redirect url with your third party
# auth service accordingly if you're using the default Vikunja frontend.
# Take a look at the [default config file](https://github.com/go-vikunja/api/blob/main/config.yml.sample) for more information about how to configure openid au>
openid:
# Enable or disable OpenID Connect authentication
enabled: true
# A list of enabled providers
providers:
# The name of the provider as it will appear in the frontend.
- name: "authentik Login"
# The auth url to send users to if they want to authenticate using OpenID Connect.
authurl: https://<Authentik URL>/application/o/vikunja/
logouturl: https://<Authentik URL>/application/o/vikunja/end-session/
# The client ID used to authenticate Vikunja at the OpenID Connect provider.
clientid: <client ID>
# The client secret used to authenticate Vikunja at the OpenID Connect provider.
clientsecret: <client secret>
scope: openid email profile vikunja_scope
# Prometheus metrics endpoint
metrics:
# If set to true, enables a /metrics endpoint for prometheus to collect metrics about Vikunja. You can query it from `/api/v1/metrics`.
enabled: true
# If set to a non-empty value the /metrics endpoint will require this as a username via basic auth in combination with the password below.
username:
# If set to a non-empty value the /metrics endpoint will require this as a password via basic auth in combination with the username below.
password:
Have everything proxied through NGINX Proxy Manger, and it works, get a redirect when going to <frontend url> that takes me to Authentik, then drops me off at the login page (though I have it disabled in my config)
running Version: v0.24.1-20-784cd42a7a
Edit3: after checking logs, looks like i had a syntax error, now i get the proper “login with authentik” but get ‘Could not authenticate against third party.’ when authentication.
logs reflect the following:
vikunja-1 | 2024-07-25T18:46:58.823746474Z: ERROR ▶ openid/HandleCallback 104 oauth2: "invalid_client" "Client authentication failed (e.g., unknown client, no client authentication included, or unsupported authentication method)"
Final edit: I messed up my clientid when pasting.